For example, if you want to search for existing directories and then fuzz within these directories again using the same payload you can use the following command:. You can modify existing headers, for example, for specifying a custom user agent, execute the following:. Wfuzz supports showing the results in various formats. WFuzz is a web application security fuzzer tool and library for Python. Wfuzz can be used to look for hidden content, such as files and directories, within a web server, allowing to find further attack vectors. If you want to fuzz some form-encoded data like an HTML form will do, simply pass a -d command line argument:. Be part of the Wfuzz's community via GitHub tickets and pull requests. 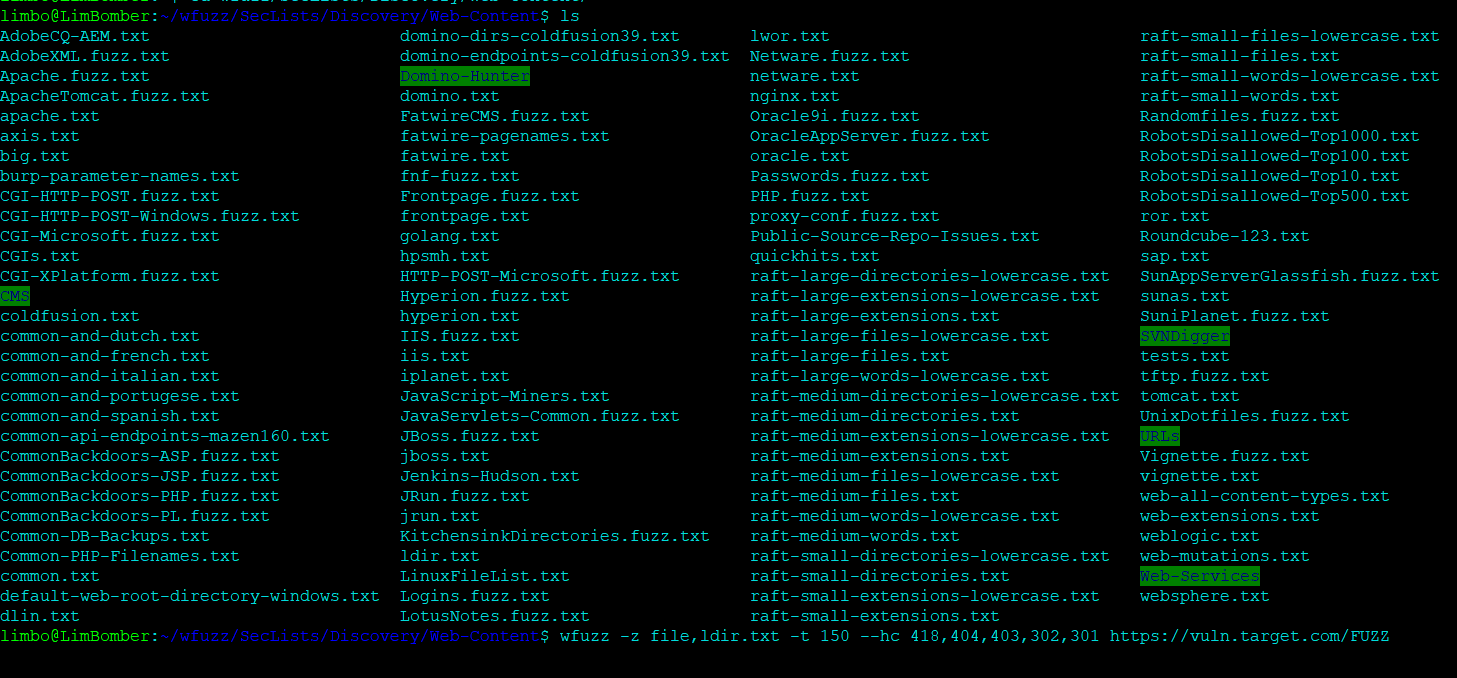
| Uploader: | Sashicage |
| Date Added: | 4 November 2016 |
| File Size: | 26.97 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 94556 |
| Price: | Free* [*Free Regsitration Required] |
If you want to fuzz some form-encoded data like an HTML form will do, simply pass a -d command line argument:.
Basic Usage — Wfuzz documentation
You can tell Wfuzz to stop a given number of seconds before performing another request using the -s parameter. You can increase or decrease the number of simultaneous requests to make your attack proceed faster or slower by using the -t switch.
WFuzz is a web application security fuzzer tool and library for Python. Several options lets you fine tune the HTTP request engine, depending on the performance impact on the application, and on your own processing power and bandwidth.
It is worth noting that, the success of this task depends highly on the dictionaries used. For example, if you want to search for existing directories and then fuzz within these directories again using the same payload you can use the following command:.
Wfuzz supports showing the results in various formats. For example, a protected resource using Basic authentication can be fuzzed using the following command:.
The web application Bruteforcer
The available printers can be listed executing:. The available printers can be listed executing: Wfuzs, brute forcing these contents becomes a more feasible task.

Be part of the Wfuzz's community via GitHub tickets and pull requests. To send your own cookies to the server, for example, to associate a request to HTTP sessions, you can use the -b parameter repeat for various cookies:. Wfuzz contains some dictionaries, other larger and up to date open source word lists are: Wfuzz can be used to look for hidden content, such as files and directories, within a web server, allowing to find further attack vectors.
Check the filter language section in the advance usage document for the available fields. However, due to the limited number of platforms, default installations, known resources such as logfiles, administrative directories, a considerable number of resources are located in predictable locations.
You can modify existing headers, for example, for specifying a custom user agent, execute the following:. Wfuzz supports writing the results to a file in a different format.
Googlebot - News Connection: For example, a protected resource using Basic authentication can be fuzzed using the following command: For example, if you want to search for existing directories and then fuzz within these directories again using the same payload you can use the following command:

Комментариев нет:
Отправить комментарий